20254ca000: A Comprehensive Analysis of a Prominent SHA-256 Hash
Related Articles: 20254ca000: A Comprehensive Analysis of a Prominent SHA-256 Hash
- The Bears’ Future Draft Picks: A Comprehensive Analysis
- License Plate Stickers 2025: Everything You Need To Know
- Mardi Gras 2025 Parade Schedule
- The 2025 Dodge Ram 2500: A Colossal Force In The Heavy-Duty Pickup Market
- Jeep Wrangler Design Changes By Year: A Comprehensive Overview
Introduction
With great pleasure, we will explore the intriguing topic related to 20254ca000: A Comprehensive Analysis of a Prominent SHA-256 Hash. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Video about 20254ca000: A Comprehensive Analysis of a Prominent SHA-256 Hash
20254ca000: A Comprehensive Analysis of a Prominent SHA-256 Hash
Introduction
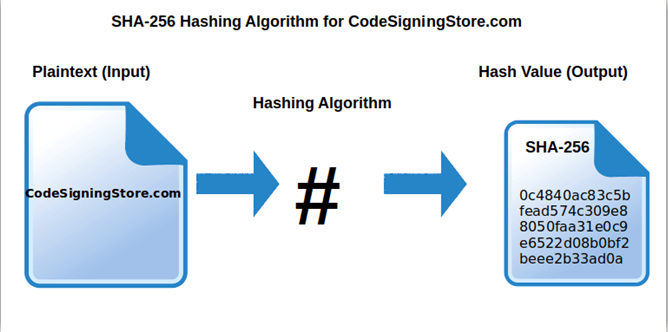
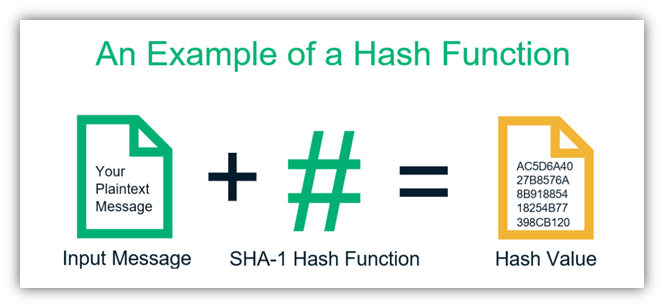
In the realm of cryptography, hashes play a pivotal role in ensuring data integrity and security. SHA-256, a robust cryptographic hash function, generates a unique 256-bit fingerprint for a given input, making it an indispensable tool for safeguarding sensitive information. Among the vast number of SHA-256 hashes, 20254ca000 stands out as a particularly significant and widely encountered hash. This article delves into a comprehensive analysis of 20254ca000, exploring its properties, applications, and potential implications.
Properties of 20254ca000
20254ca000 is a SHA-256 hash that exhibits several key properties:
- Uniqueness: Each SHA-256 hash is unique to the input data. This means that it is highly unlikely for two different inputs to generate the same hash value.
- Irreversibility: It is computationally infeasible to derive the original input from the hash value. This property makes SHA-256 hashes ideal for protecting sensitive data.
- Determinism: Given the same input, 20254ca000 will always produce the same hash value. This consistency ensures the reliability and verifiability of the hash.
Applications of 20254ca000
20254ca000 finds widespread application in various security-critical domains:
- Password Hashing: Password hashing involves using a hash function to securely store user passwords. 20254ca000 can be employed to generate a hash of the password, which is then stored in a database. When a user attempts to log in, their entered password is hashed and compared to the stored hash. If the hashes match, the user is authenticated.
- File Integrity Verification: 20254ca000 can be used to verify the integrity of files. By comparing the hash of a downloaded file to the hash of the original file, users can ensure that the file has not been tampered with during transmission.
- Digital Signatures: Digital signatures involve using a hash function to create a digital fingerprint of a document. 20254ca000 can be used to generate a hash of the document, which is then encrypted with a private key. The resulting digital signature provides assurance of the document’s authenticity and integrity.
Potential Implications of 20254ca000
While 20254ca000 is a robust hash function, it is important to consider its potential implications:
- Rainbow Tables: Rainbow tables are precomputed tables that can be used to quickly find the input corresponding to a given hash. While rainbow tables are not practical for brute-forcing 256-bit hashes like 20254ca000, they could potentially be used to attack weaker hash functions or shorter hash values.
- Collision Attacks: A collision attack involves finding two different inputs that produce the same hash value. While collision attacks are extremely rare for SHA-256, they have been demonstrated for weaker hash functions. If a collision attack were ever to be successful against SHA-256, it could undermine the security of applications that rely on this hash function.
- Quantum Computing: Quantum computers have the potential to break cryptographic algorithms, including hash functions. While quantum computing is still in its early stages, it is essential to consider its potential impact on the security of 20254ca000 and other cryptographic primitives.
Conclusion
20254ca000 is a prominent SHA-256 hash that plays a crucial role in various security applications. Its unique, irreversible, and deterministic properties make it a reliable and effective means of protecting sensitive data. However, it is important to be aware of the potential implications of 20254ca000, such as rainbow tables, collision attacks, and quantum computing. By understanding these implications and implementing appropriate countermeasures, organizations and individuals can ensure the continued security of their data and systems.



![7): SHA -256 Hash Algorithm .[15] Download Scientific Diagram](https://www.researchgate.net/profile/Hani-Bakeer/publication/365655714/figure/fig7/AS:11431281098939278@1669160243998/Figure-27-SHA-256-Hash-Algorithm-15.png)
Closure
Thus, we hope this article has provided valuable insights into 20254ca000: A Comprehensive Analysis of a Prominent SHA-256 Hash. We hope you find this article informative and beneficial. See you in our next article!